| 精华 | |
| 金钱 | BA |
| 威望 | 点 |
| 贡献值 | 点 |
| 爱心 | 点 |
| 经验 | 点 |
| 注册时间 | 2015-8-8 |
| 最后登录 | 1970-1-1 |
| 在线时间 | 小时 |
| |
| |
| |
|
立即注册,加入爱黑武论坛的大家庭!爱黑武,爱上搞机生活!
您需要 登录 才可以下载或查看,没有账号?注册
x
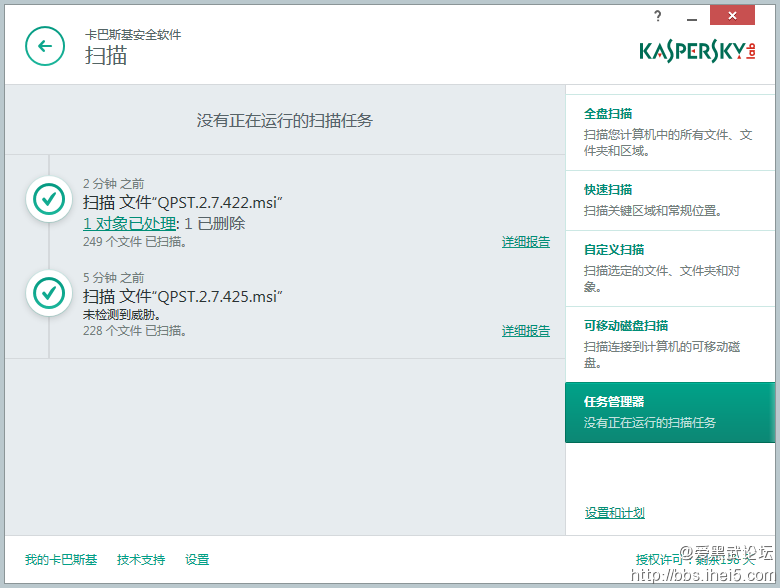
本来看尘封的教程下载QPST
http://bbs.ihei5.com/thread-328434-1-1.html
结果KIS跳了,卡巴误报的情况真的不多,平时都安静的不行
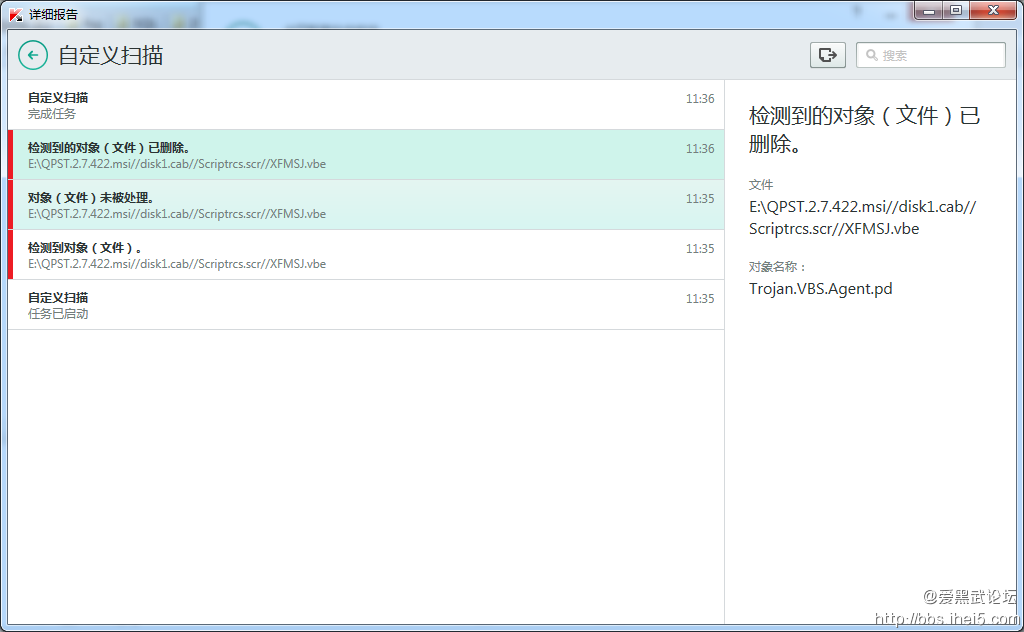
结果在XDA看到有人说422版本有问题,实际是402改的,加了个keylogger
http://forum.xda-developers.com/showthread.php?t=2263391
- Hello, fellow QPST users.
- QPST 2.7 Build 4.2.2 is a fake version with keylogger.
- Some a$hole downloaded latest public QPST build (4.0.2) and decompiled MSI installer package, then edited all "4.0.2" to "4.2.2", added "fake changelog", added keylogger (qualcomm.exe), then repackaged and spread around web!
- Everyone who downloaded QPST build "4.2.2" should change all his passwords.
- More info about malware from fake 4.2.2 build (QPST.2.7.422.msi)
- MSI package (QPST.2.7.422.msi) was embedded/tampered with qualcomm.exe which is a .NET based malware that logs your keystrokes and sends it to attacker's server.
- How to delete the actual malware from your system?
- Look at the startup from msconfig or CCleaner, there should be a file called qualcomm.exe thats set to start everytime system starts. Delete both registry and file.
- If you wanted to see what data thief was stolen from you. Just open the .dc file (in "dclogs" folder) with Notepad and see for yourself.
- In XP, dc file is located here!
- C:\Documents and Settings\Administrator\Application Data\dclogs
- there should be a file called "201X-XX-XX-X.dc
- if you open that DC files with Notepad, you'll see all your keystrokes.
- Here is mine. I've intentionally entered paypal site with fake info.
- Quote:
- :: Run (3:01:51 AM)
- Script kiddie. NET Based malware, huh?[ESC]
- :: Program Manager (3:02:14 AM)
- e
- :: Firefox (3:02:18 AM)
- www.paypal.com
- johhny193@yahoo.com[TAB]
- mypaypalpass
- [ENTER]
- :: Documents and Settings (3:02:19 AM)
- [UP]
- :: Administrator (3:02:28 AM)
- [DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN]
- [DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN][DOWN]
- d
- :: (3:02:34 AM)
- :: Administrator (3:02:34 AM)
- d
- :: (3:03:11 AM)
- mmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmm
- :: [Release] QPST 2.7 BUILD 422 - Download Here - Enjoy - Mozilla Firefox (3:03:57 AM)
- crap
- How to delete?d
- :: Clipboard Change : size = 16 Bytes (3:03:57 AM)
- QPST.2.7.422.msi
- :: (3:04:23 AM)
- cccccc
- Keylogger sends the logs from keylogger to "qpst.hopto.me"
- So please report about this incident where and when you encounter QPST 4.2.2 somewhere (forums, posts, sharing-sites, etc)
- Copy my whole post and paste it where you see 4.2.2 mentioned.
- Bonus: Fake Changelog
- If you've installed this 422 build, then open the Readme.txt in C:\Program Files\Qualcomm\QPST\Documents
- Scroll down and see the "6/12/13 QPST 2.7.422 changelog"
- Quote:
- 6/12/13 QPST 2.7.422
- 1) EFS Hello commands will not be sent unless the device is in a compatible mode. Sending this command when the
- device is in download mode can cause a "server busy" message for a few seconds because of command retries.
- 2) Support for the Sahara device protocol (see 80-N1008-1 or equivalent) is now built in to the QPST server process.
- This protocol is only supported by USB Serial ports, not TCP/IP connections. In QPST Configuration a device in
- this mode will display as "Q/QCP-XXX (Sahara Download)". This mode can only be detected (1) when the QPST server
- process starts or a COM port in this mode added to QPST, or (2) when a device enters Sahara mode on a port assigned
- to QPST. This is because the device only sends its Hello message once, as soon as the COM port is opened.
- Changelog above is actually cloned from QPST 2.7.394 Just scroll down and see Build 2.7.394 changelog. Its same!
- So forget about Build 422. It doesn't exist.
- Use QPST 2.7 Build 402. It's the latest public build
这里也有讨论:
http://cdmagurus.com/archive/index.php/t-17103.html
但是,说422有问题的人发的411链接,经验证也是有问题
- !!!!!!!!!!!!!!!!!! WARNING !!!!!!!!!!!!!!!!!!
- !!! TROJAN AGAIN !!!
- Some time ago in Feb 2014 man named anycallmongolia posted a link to QPST 2.7 build 411
- Link points to the site HuaweiDevices.ru
- h_t_t_p_://_huaweidevices._ru/ROMS/QPST_2.7.411.rar
- Later I'd personally downloaded this version from this topic a few times in 2014 and this was normal non fake QPST which i'd installed on a few PC's. (Can't remember particular link now). Today I would like to install QPST to a new NB PC, so assumed this topic as the best source. Being a recovery/data structures expert I always inspect code (mostly by viewing in text/hex). As most of members I've very high trust level to xda (certainly it's much higher then one related to the "famous and respectable" corps like Google/MS/Apple/etc, who aren't on my side, I'm sure).
- I've installed QPST got from this topic a few times, so I'd almost pressed Enter (I use FAR most of time and advice you to do the same) over the DL'd file "qpst 2 7 411.exe".... What??? - EXE??? And it's just about 500Kb long... But QPST installer occupies about 16Mb.
- I've explored body - I's typical malware with slightly "encoded" (to prevent direct reading) data inside. QXDM offered on the neighbor page is the same malware of the same size.
- If you'll try to dl QPST from above link you'll got 404 error in the center of normal html page with site menu etc... What normal man would think in this case? He'll think page/product have moved (e.g. due to overload protection) and what he'll do next? He'll try to find where page have moved and... will got link in menu just at the bottom of 404 page. It's just trivial (but very good working!) "social engineering" - publish real app in trusted place and when it will pass checks replace it with malware. (Or may be domain was sold to the criminals as it often occures in Russia for a few latest years). Even if you will check DL url in the status bar it will show link to the .RAR archive, but ASAY click the link it will be redirected to .exe!
- PLEASE PUBLISH BIG WARNING on TOPIC START and remove links to HUAWEIDEVICES.RU!!!
- Furthermore. Situation is much worse because huaweidevices shows 1ST position in search request "QPST 2.7.411" by Yandex.ru (#1 search engine in Russia) and 2ND position in Google results with the same request!!! It's VERY DANGEROUS situation! Thousands if not millions of peoples are at risk of infection.
- I'm going to write abuses to Google and Yandex NOW!
- Please spread info on such a new attack manner/technique around your friends, collegues and internet.!
- Always check what you run!!!
后面有人发了425版本,KIS扫描没问题,但网络险恶,我也不能保证425没有问题,还请谨慎使用,用个电信手机真不容易,蛋!
- http://www.mediafire.com/download/neeapht51ub2333/QPST.WIN.2.7_Installer-00425.1.zip
|
-
-
|
 /1
/1 